The problem of collaboration – does the modern working environment requiring a new approach to Data Loss Prevention?
The modern post-Covid workplace has created an unstoppable drive for more collaboration and productivity tools. There is a plethora of options on the market, all of which describe themselves as helping businesses to work more efficiently and effectively, particularly with a remote or hybrid workforce. While this might seem great for many firms, the question that IT and cyber professionals might want to ask is whether this desire for collaborating in the cloud has created a ticking time bomb in terms of information security and data privacy.
If you are reading this as someone with a vested interest in technology – either due to this being your area of expertise or responsibility, or just as something you find personally intriguing – this is a question that should give you significant pause for thought. Given the prevalence of Microsoft’s Office 365, it might also be worth asking yourself, presuming your organisation has rolled this solution out:
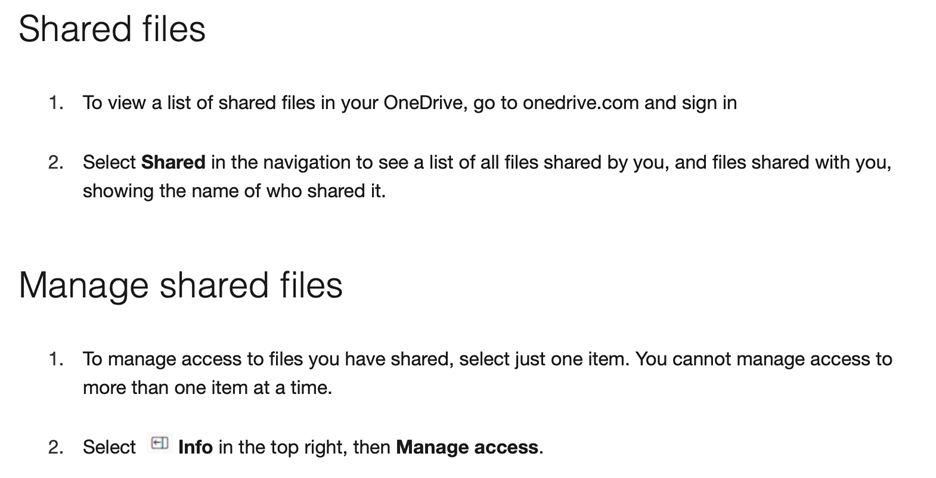
- How many files have you shared using OneDrive or Teams – can you quickly find out?
- Do you know how to quickly un-share documents, or numbers of documents?
Both are critical to answer, but the solution for number 2 (shared below) is hardly user friendly:
The issue of literacy and awareness
Considering the fact that collaboration software is now so ubiquitous, it might be worrying that something as seemingly simple as un-sharing is such an involved process. While the tech savvy amongst us might consider this trivial and not excessively convoluted, it is important to remember that tech literacy is not universal.
Spreading awareness of anything technical – particularly where there is a direct requirement for users across an organisation to perform specific, regular actions – is no mean feat. Users need to understand not only ‘what’ is required of them but also ‘why’ to achieve full buy-in, and this is by no means a formality. As a result, the chances that the average user has reviewed their shared files (either due to ignorance of how to do this or of the importance of doing so) are likely to be exceptionally low.
Many organisations do not grasp the scale of document sharing that is taking place within their environment. This phenomenon is exacerbated when large complex organisations operate across multiple tenants where there are either trust relationships between them or large numbers of guest users.
These ‘guests’ (typically external users) will often have unclear access permissions, given access without being subject to formal Joiner/Mover/Leaver (JML) controls, and often subject to limited (if any) review. These factors, especially in the context of sharing being so easy and so widely encouraged, create a potential maelstrom of risks for an organisation that would make anyone managing supply chain risk baulk.
The real-life cost of not having Data Loss Prevention
One counter to the concern over collaboration tools would be to raise the example of email. Some might ask whether, given that once an email with an attachment is sent and control over it has been lost forever (unless you are using documents rights management solutions which, in and of themselves, have their own challenges), is this not exactly the same problem described above? And, given we by and large accept the risk of email, why should we be more concerned about data loss in the context of collaboration tools?
This is unfortunately something of a fallacious comparison that can be demonstrated by some examples adapted from real-world experience:
- Persistence (the file remains shared until unshared): The first issue we have with collaboration tools is that, due to human error, it is easy to forget that a file has been shared and remains accessible to a third party. For instance, imagine an example where a team shares pricing information with their client via excel spreadsheets. It is not a stretch that, making the most of sharing capabilities, this spreadsheet is then shared with the client for ease. But what if this functionality is not removed and the file is never ‘un-shared’? Following this example, if the internal team used the same file to do some modelling for other clients (for instance, including very sensitive commercial information as well as some ‘choice comments’ in a few cells from a management review) this would also be seen by the original recipient of the pricing spreadsheet. Not only is this a breach, but potentially highly embarrassing and resulting in some difficult conversations.
Ask yourself if you’ve ever gone back to a presentation or file to reuse it for a new situation and then not realised it was still shared.
- Proliferation (the share that continues to be perpetuated): Losing control of files is also a significant risk in these situations, especially where a file is shared extensively to individuals in circumstances where the original creator/owner is unaware of how many individuals can see it. In this scenario, we can imagine that a manager has been working on a strategy presentation and wants to share an early version with some of the senior management for comment and input. One of those senior leaders then might share the presentation with another member of her team to add some more data. At this point, that share is likely to be approved by the owner of the document without really questioning it (something that could be termed the ‘click yes on the request’ reflex). However, at this point, unless access is reviewed at a later point, control is lost. Imagine if a later version of the strategy involved a restructuring of the team with which the strategy was shared. How long would it be before that became public or at least its contents were widely distributed?
Ask yourself if you’ve every inadvertently accepted a share request because it probably seemed reasonable at the time – and if you did, did you revoke it?
- Prodigiousness (the share can be more than just a file): Another huge pitfall with regards to collaboration is that, with it being so easy to do, it’s not hard to ‘over-share’ and distribute much more than just the file you intend to or consent to this proliferation happening. An example that illustrates this point consists of a case where poor management judgement is combined with one of the more powerful (and dangerous) aspects of sharing, the ability to share a folder rather than just a file.
In this case, a contractor is working on a graphic design for an upcoming rebrand and strategy refresh on behalf of their client. The contractor decides that his company-supplied desktop isn’t good enough and he would be happier working on his MacBook at home – consequently, he shares his entire documents directory to his personal email address. In this scenario, the nature of the project he is involved in means that he has, in that drive, copies of the upcoming strategy, branding and other very sensitive data.
Following this, the company insider threat team identifies the issue as part of manual sweep for shares to ‘personal-looking’ email addresses (e.g., Gmail, Hotmail etc.). An incident is raised and investigated, part of which results in the user removing that sensitive information from their MacBook where they had copied all those files for quicker access to them. In this case, it turns out that the contractor’s line manager has approved the sharing the data to a personal device, although the manager had no understanding of scale of what had been shared and the potential near miss that had occurred.
Ask yourself how many directory level shares are out there in your organisation and whether your line managers understand the impact of what they are approving?
All of these examples come from real client cases. They all illustrate not only how easy it is to make grave errors leading to data breaches, but also the substantial consequences of not considering data loss prevention (DLP) when implementing and using collaboration software. The potential consequences of file sharing outlined above – persistence, proliferation and prodigiousness – should always be considered and measures put in place to counter them.
Protecting data, protecting yourself
Clearly, collaboration tools are here to stay – and that should not be inherently disconcerting given the obvious benefits they provide for teams working together in the cloud, remotely or otherwise. However, companies should not be naïve about the potential adverse impact of these tools.
There are many things organisations can do to protect their data from inadvertent loss – monitoring, limiting sharing, document rights management solutions – but ultimately, as the examples above show, many of the issues come from individual behaviour, which means any organisation will need to work hard to ensure that awareness of risks and correct behaviours is spread across all staff.
Should an organisation be worried about data that is being shared by users, starting with an investigation and data mapping exercise will certainly help understand the scale of the problem. Following this, the temptation might be to rush to a technology solution – however, this would be unwise without a proper strategy, policy and set of procedures around DLP, and then the correct buy-in from all individuals in the business.
Collaboration is a brilliant thing and ultimately helps businesses operate more smoothly. However, there is also an Achilles heel that you must consider. When sharing is haphazard and uncontrolled, you can and will lose control of your data. For that reason, a carefully considered strategy and approach to DLP is vitally important.
How we can help?
If you would like to understand more about data privacy and protection, get in touch to arrange a free consultation with one of our experts today.


