Introduction
At Reliance Cyber, our Incident Response and Extended Detection and Response (XDR) teams recently observed a concerning evolution in Business Email Compromise (BEC) tactics. These attacks are no longer just about phishing links reaching unsuspecting employees; they are exploiting trusted workflows and automation within secure environments, slipping through traditional security defences in ways rarely anticipated. Microsoft 365’s security controls, like Zero-hour Auto Purge (ZAP) and advanced anti-phishing filters can detect and flag these emails, yet BEC actors are now leveraging internal email rules and automated processes to bypass them. By targeting generic email addresses and infiltrating secure systems through ticketing platforms, they reveal a crucial vulnerability in organisational defences that merits attention.
Understanding Business Email Compromise (BEC)
The MITRE ATT&CK[1] framework defines BEC as a social engineering attack where threat actors use email to deceive businesses or individuals into authorising financial transactions or revealing sensitive information. These attacks leverage the trust within organisational processes, using impersonation and urgency to compel quick, unverified actions. In contrast to broad phishing campaigns, BEC attacks are precise, often based on extensive research about the organisation and its key personnel. A threat actor may impersonate a senior executive or trusted partner, pressuring the recipient to act without delay. The result is usually significant financial loss, such as unauthorised fund transfers, data theft, or rerouting of payments to fraudulent accounts.
Real-World Impacts
The FBI’s Internet Crime Report has documented BEC attacks, as having caused nearly $2.9 billion in losses in 2023, highlighting the substantial risk posed by these highly targeted attacks. Real-world cases, including incidents involving Scoular Co. in 2014, Puerto Rico’s Government in 2020, and the Treasure Island Charity, underscore the significant costs of BEC tactics. By exploiting trust and urgency, these attackers manipulate decision-makers and financial teams into taking costly actions with long-lasting effects.[2][3][4]
Abstract
Reliance Cyber Incident Response and XDR teams have recently observed a sophisticated wave of phishing attempts that slip past the M365 environment’s security controls and ultimately engage unsuspecting employees. Even within what are typically considered secure settings, these emails, flagged as phishing or spam, are enticing employees to interact with malicious content.
A particularly effective technique involves targeting publicly accessible generic email addresses, such as accounts@company.com, finance@company.com, or HR@company.com—addresses that often see a high volume of external interactions and are easy to guess for threat actors. During triage and full analysis, these generic accounts are frequently found to be an entry point for phishing attacks. Once in the system, phishing emails are forwarded internally, triggered by mailbox rules that re-route the malicious message to another private, internal mailbox. For instance, a phishing email initially delivered to accounts@company.com might be automatically forwarded to invoicing@company.com, allowing it to bypass additional scrutiny and reach new recipients.
Our teams have uncovered multiple cases where these forwarded emails initiate automated processes, slipping into ticketing systems that create service tickets based on email content. In environments where systems like Freshdesk and ZenDesk are employed, this automated ticket generation workflow can inadvertently escalate the phishing email’s reach within the organisation. Here, ticketing systems often assume a ‘safe’ environment, giving employees an unguarded view of the phishing link or attachment—a setup ripe for clicks.
In our recent analyses, the attackers managed to embed themselves within internal systems simply by taking advantage of these established workflows. Phishing emails often landed in the inbox or junk folders of various recipients, flagged as either spam or phish by M365 controls like Zero-hour Auto Purge (ZAP). But even though these security measures attempted to quarantine the threat, internal rules were triggered before full security actions could take effect. In this brief window, the phishing email’s content was forwarded, making its way into internal workflows and resulting in auto-generated tickets.
Observed Process
Despite M365’s robust protections, traditional security measures can be circumvented by internal email routing rules.
Internal Routing and Forwarding Rules
Email rules, including Exchange transport rules, are often executed immediately upon email receipt. While ZAP flags malicious emails, we’ve observed internal routing rules forward these emails to other mailboxes or external systems like Freshdesk before the security controls fully apply.
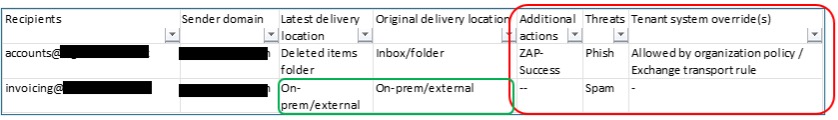
In the Unified Audit Log (UAL) output, the Tenant system override(s) attribute with the value Allowed by organization policy / Exchange transport rule indicates that the action taken on the email was permitted due to a policy or rule configured within the organisation’s Microsoft 365 tenant.
- Exchange transport rule: This indicates that a transport rule (also known as a mail flow rule) configured in the organisation’s Exchange Online environment allowed the email. Transport rules are used to manage and modify email messages as they pass through the Exchange environment, and they can be set up to bypass filtering based on specific criteria, such as sender, recipient, or content.
- The Latest delivery location and Original delivery location attributes relating to the value On-prem/external indicates that the email is forwarded to an external email system not managed by Microsoft 365, in this instance, Freshdesk.
- The ZAP (Zero-hour Auto Purge) security control in Microsoft 365 is a feature designed to protect users from malicious emails that bypass initial filtering. It automatically removes (or “purges”) potentially harmful emails, such as phishing or malware-laden messages, from users’ inboxes after they have been delivered if they are later identified as threats.
Security Controls – Gaps In The Armour
- M365 Marking, but Not Blocking: Although M365 flagged the emails as spam or phishing, internal routing systems allowed these flagged emails to continue through other channels. The emails bypassed traditional defences because of internal redirection rules, which let them enter the M365 accounts where the ticketing system would be initiated prior to them being flagged as malicious.
- Inbound Email Flow: When an email is received by an M365 mailbox, it goes through a series of processing steps before it reaches the recipient’s inbox.
- Initial Delivery: As soon as an email is received, it is subject to basic routing and filtering. Mailbox rules configured by the user are executed immediately based on predefined conditions.
- Content Scanning (Anti-Spam, Anti-Phishing): After the initial routing, the email goes through more advanced security mechanisms, such as anti-spam and anti-phishing checks, which scan the content, attachments, and links to determine if the email is potentially malicious.
- Execution at the Routing Stage: M365 email rules (such as inbox rules or transport rules) are processed early in the pipeline—often before more in-depth content scanning. These rules are based on easily identifiable characteristics, like sender address, subject line, or recipient, and they are applied immediately when an email is routed to a mailbox.
- Ticketing Systems’ Automation Flaw: The ticketing system automation inadvertently escalated the phishing email’s legitimacy by creating a ticket, which could then be view or acted upon by internal department members. Individuals can then click the phishing link, which, in cases observed by Reliance Cyber, led to a static malicious page hosted on a cloud platform. This ultimately redirected them to a fake Microsoft 365 login page, where individuals their credentials, believing it was necessary to view an invoice, HR or account document.
Exchange Online Protection
Exchange Online Protection (EOP) protects your organisation against spam, malware, phishing and other email threats. EOP is included in all Microsoft 365 organisations that have Exchange Online mailboxes.[5]
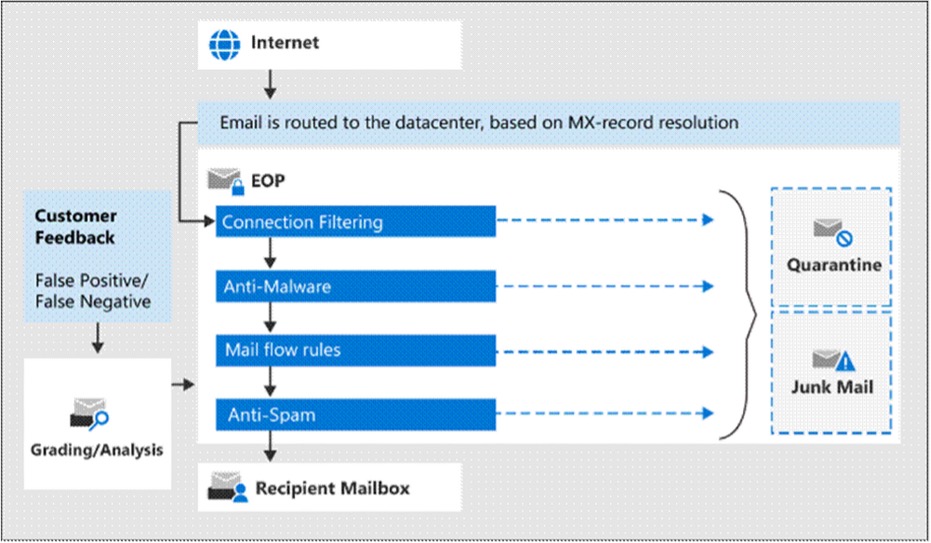
How it works
- Connection Filtering: Messages are initially filtered based on the sender’s reputation. Most spam is rejected at this stage.
- Malware Filtering: Messages are scanned for malware, and any detected are quarantined. By default, only administrators can access these quarantined items, but quarantine policies allow admin-defined user permissions.
- Policy Filtering: Messages are evaluated against custom mail flow rules (transport rules) that can trigger specific actions, such as notifying a manager of certain incoming messages.
- DLP Checks (for on-premises organisations with Exchange Enterprise CAL with Services licences): Microsoft Purview Data Loss Prevention applies additional security checks.
- Content Filtering: Anti-spam and anti-spoofing checks categorise messages as spam, phishing, or spoofed. Actions, such as quarantining or moving to Junk, can be configured based on the filtering results, with policies set to control user interaction with quarantined items.
Weaknesses in Existing Security Processes
The reliance on automated workflows in email handling and ticketing systems has several inherent weaknesses that can be exploited by BEC attackers:
Forwarding to Generic Email Addresses
When emails flagged as phishing are forwarded to other internal or external systems, they can re-enter workflows designed to aid productivity but inadvertently expose organisations to risk.
Execution Timing of Email Rules
M365 email rules and Exchange transport rules are applied early, meaning that emails may be routed before in-depth content scanning is complete. Attackers exploit this timing to ensure their emails reach sensitive workflows unimpeded.
Assumptions in Ticketing System Security
Many ticketing systems are configured to process all internal emails without further scrutiny, assuming these are legitimate. This trust in internal processes allows flagged phishing emails to become trusted tasks, reinforcing the threat actor’s position. In cases we observed, employees accessing the ticket were redirected to phishing sites, such as a fake M365 login page, where their credentials were stolen. This approach creates a dangerous path for BEC actors to gain deeper access within the organisation, often without immediate detection.
Mitigation Strategies: Strengthening Defences
To prevent such attacks, organisations need a layered approach combining security, workflow adjustments, and employee training:
Refining Email Routing and Handling Protocols
Review email forwarding rules and implement conditional access to limit email routing until after a full security check. This reduces the risk of flagged emails bypassing critical checks.[6]
Safe Links and Safe Attachments
Microsoft’s Safe Links and Safe Attachments provide continuous scanning of emails even after delivery, reducing the likelihood that malicious links or attachments are acted upon.[7]
Enhanced Security in Ticketing Systems
Ticketing systems should be configured to flag or require manual review of any ticket generated from a flagged email. Integrating an additional security layer here would prevent phishing emails from being immediately accessible in internal workflows.
Conditional Policies
Microsoft 365 allows for Conditional Access rules that can delay or block email forwarding until an additional security check is completed. This approach would prevent flagged emails from automatically being routed to ticketing systems without further scrutiny.[8]
Rethinking Secure Workflows
The breakdowns observed in this BEC attack highlight the need for a comprehensive review of email routing, ticketing workflows, and automation. Allowing phishing emails to navigate internal systems unchecked leaves organisations open to serious risks. To mitigate these threats, organisations must invest in refining email handling policies, implementing conditional access controls, and ensuring robust ticketing platform security.
Conclusion
The rising threat of Business Email Compromise underscores the critical need for vigilance in email and ticketing workflows, where automated processes and internal trust are being exploited by attackers. Our investigations reveal that even trusted, ‘secure’ environments can be compromised by sophisticated attacks targeting automated processes and organisational trust. Organisations can counter these risks by implementing refined email routing rules, securing ticketing systems, and training employees to recognise signs of compromise.
By addressing these vulnerabilities holistically, organisations can foster a culture of cybersecurity awareness and enhance resilience against the ever-evolving tactics of BEC actors, ultimately safeguarding their operations in today’s high-stakes cyber environment.

Eoin O’Keeffe
With over 19 years of experience spanning public and private sectors, Eoin is a seasoned cybersecurity professional specialising in cyber threat intelligence, incident response, digital forensics, and digital risk management. Eoin has established and led comprehensive Cyber Security functions, managed complex cyber investigations within the public and private sector, and developed strategic cybersecurity roadmaps for global organisations.
Eoin has a proven track record of delivering within complex cyber incidents, conducting detailed investigations, and developing tailored cybersecurity solutions. With hands-on experience in threat detection, forensic analysis, and the mapping of adversary tactics, techniques, and procedures (TTPs), Eoin brings a deep, technical approach to enhancing security postures and safeguarding organisations against evolving threats.
[4] Business Email Compromise (BEC) Attacks
[5] Exchange Online Protection (EOP) overview – Microsoft Defender for Office 365 | Microsoft Learn
[6] Scenario Conditional mail routing in Exchange Online | Microsoft Learn
[7] Complete Safe Links overview for Microsoft Defender for Office 365 – Microsoft Defender for Office 365 | Microsoft Learn
[8] Getting started with defense in-depth configuration for email security – Microsoft Defender for Office 365 | Microsoft Learn

