It is well established that the majority of cyber attacks on organisations use email. These attacks are becoming more complex and sophisticated, with hackers routinely using social engineering deception (phishing) to target employees, bypass security gateways and deliver malware.
The consequences for small to medium businesses are often significant. Ransomware can shut down operations, impacting businesses’ ability to fulfil contracts. Average recovery costs double every 12 months, and 80% of those who pay ransom fees are subsequently targeted again.
98% of UK companies suffered some sort of IT security incident in the last 12 months – who operate outside of well protected perimeter security measures – left more exposed to web-based attacks. With so much sensitive information stored on the cloud today, these priceless details are more accessible than ever.
At Reliance Cyber, we support our customers to stay ahead of cybercriminals, so you can protect your business and stay focused on your core commercial activities. Below are our top three tips for small to medium business to improve their Office 365 security.
- Turn off single factor authentication for legacy authentication protocols
Legacy authentication can be supported within Office 365 and may be used for protocols and clients where multi-factor authentication is not supported. Its default policy is configured to allow this globally for all users on legacy protocols, such as IMAP, POP3 and Autodiscover.
Here’s how:

The Reliance Cyber MDR team sees attempts to exploit this deprecated authentication means on a daily basis. In the past 30 days alone, we have identified two major incidents in which basic authentication was exploited successfully, and a user account compromised as a result.
2. Monitor organisational patch and support levels for device health
Microsoft releases patches for its operating system products on the second and, sometimes, the fourth Tuesday of each month. These are informally known as ‘Patch Tuesday’ within the industry and should be marked on your calendar, so that any post-release vulnerability or flaw can be repaired promptly.
The company has two tiers of operating system support. While the product is under mainstream support, Microsoft will continue to release security updates for it; additionally, it will accept feature requests and implement these as patches and service packs. When a product falls out of mainstream support, it enters extended support, which means it will no longer receive feature updates and only get security ones. Once the end-of-life date arrives, the product will no longer receive any support and, therefore, will become unsupported.
Here’s how:
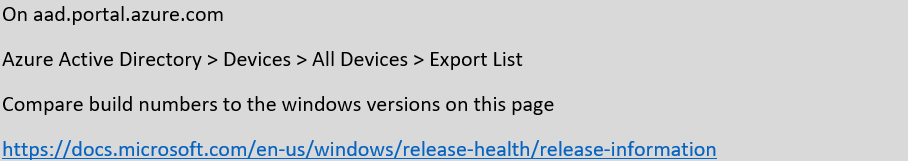
Also configure data retention policies to ensure that old, cached devices are purged, having not been seen for six months.
3. Enable Basic Mobility and Security
Basic Mobility and Security is a Microsoft feature that is part of Office 365’s basic tier tenancy. Configuring these settings allows administrators to ensure that the user sets a passcode to the prescribed strength before they can receive outlook mail on their mobile devices, be they corporate or personal systems.
Administrators can also dictate whether this is either a numeric pin of a minimum length or an alphanumeric passcode on the device.
In addition, they can mandate that devices are encrypted and that they force reauthentication after two minutes of inactivity on admin accounts and ten minutes for standard users.
Here’s how:

As organisations in all sectors come under increasing pressure from cybercriminals, reducing the chances of an attack must be high on everyone’s agenda. Prevention is better than cure and these precautions will do much to tackle the rise in malicious hacks.
Reliance Cyber can help you meet all the cyber security challenges with confidence. Get in touch to arrange a chat about better protecting your organisation.

