A common strand of activity for us here at Reliance Cyber surrounds Incident Response; helping existing customers to manage security incidents or helping new customers to respond to incidents when they occur.
In 2022, we helped organisations handle thousands of security incidents. The precise number that transited the Security Operations Centre (SOC) was 77,532 – in addition to a small number of more serious incidents experienced by our non-managed service customers, which are described below. Of those, a small percentage were of sufficient severity that notifying insurers and/or the Information Commissioner’s Office of a potential Data Breach became necessary. When that happens, and once the incident is remediated, we work to establish and resolve the root cause.
The Root Cause Analysis can be broken down as follows:
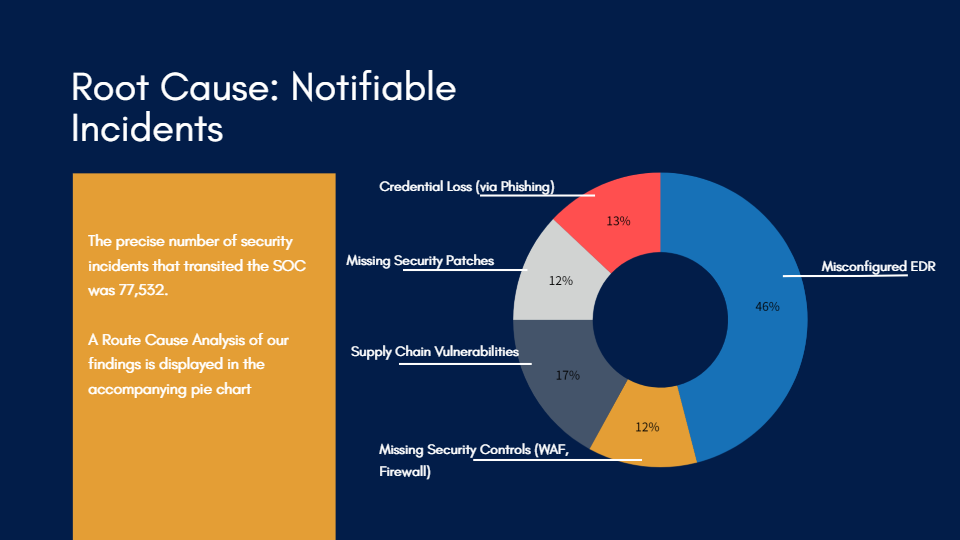
All of the areas above are deserving of discussion (watch this space), but, today I want to focus on EDR. In particular, Microsoft’s Defender for Endpoint – though the lessons can be easily applied to other similar tools.
The key point is this: Defender for Endpoint is not something that you can buy, install and leave to do its job. It is a very complex and sophisticated suite of security products that are incredibly effective, but only when properly deployed, configured and monitored. Achieving an appropriate deployment is not something that most organisations organically have the capacity to do well – not unless you have specifically recruited and trained for that expertise.
Four Key Considerations When it Comes to EDR…
Let’s take look at some examples of the key questions that will undoubtedly arise when you start to consider EDR:
- Licensing.
- Do you need Plan 1 or Plan 2?
- Which version of Defender for Endpoint is included in your existing E3 and E5 plan?
- What are the full suite of features in each and do you need them?
- Can you install it on servers – and if so how?
- What’s the best way to buy the licenses?
- Deployment – Assuming that you don’t have an unlimited budget;
- Where is the priority for coverage?
- Do you need to cover the entire estate, just user endpoints, or just core servers?
- How will you actually deploy it?
- Do you have Intune, or will you need to perform a more manual roll-out?
- Configuration.
- Where are the settings?
- There’s the Defender Console but Intune also has some settings, which are important?
- Should you have different policies for different types of machines?
- How can you easily assign them to each?
- What’s best practice for servers and how does that differ from user endpoints? What else should you switch on besides malware protection?
- Monitoring.
- Once deployed, how will we handle the output?
- Can we automate some of it or should it all be manual?
- Do we have playbooks for these?
- Who in the organisation will be responsible and accountable for maintaining the playbooks and modifying them to meet new threats?
- Who will be responsible for investigating alerts and deciding if they’re serious or trivial?
These questions are difficult and often there is no clear answer. Like any security solution, it depends on the business risk, the budget, and the environmental context.
For the unfortunate customers in my pie chart above, things had not been properly deployed. The tool existed on the affected hosts, but it was generating alerts that were queued with an internal team, rather than automatically isolating malicious files and defending the rest of the network. This means that Defender could have contained the problem, rather than generating an alert which requires human intervention.
In some cases, IT teams were unaware of the granular EDR and Attack Surface reduction settings available in Intune. In exactly half of the cases, moving a single toggle from ‘disabled’ to ‘enabled’ (or – more commonly – ‘Audit’ to ‘Block’) would have prevented breaches that cost tens of thousands in remediation efforts.
In other cases, entire functions of the platform were disabled and labelled as future projects – in particular Web Protection; Microsoft’s excellent inbuilt web content filter.
For EDR to be truly successful, you need access to a team who know what they’re doing and who understand the context of your environment.
With esoteric and outdated guides and forum posts sprawled across the internet, unfortunately this is one example where even Google is of limited assistance. Having tried and tested expertise is the solution to the myriad problems listed above, particularly when this expertise is sourced from a diverse range of backgrounds and experience.
Our Top Five Tips For EDR Success
When you are considering EDR, these are the key things you should look for from a cyber security provider:
One-off reviews.
If you have deployed Defender for Endpoint, or any other EDR tool, you will need a dedicated team of experts that:
- Investigate, review, and advise on best practice relating to your EDR platform.
- Provide you with documented guides and recommendations for improvement and revisit these guidelines periodically, to help ensure that any changes are managed correctly.
- Address the business risk and technical deficiencies simultaneously.
Managed Services.
The team in charge should:
- Deploy and support your EDR tool of choice – leaving your internal security teams empowered to respond to the curated output using best practice playbooks.
Or
- Deploy, support, and monitor your EDR tool of choice for you. They should deploy and align your EDR tool in line with best practice, and send the alerts to their SOC to triage, investigate, contain, and isolate on your behalf.
If you haven’t already, I encourage you to consider the above and to act quickly.
A single review may cost you some small percentage of your budget today, but not doing so may cost weeks of pain in recovery, commercial and reputation damage, and some hard-learned lessons tomorrow.
Would you like to speak with an expert about something you have read in this article?
If you want to learn more about how the team at Reliance Cyber can support you with our range of Managed Security Services, or you just need some advice, get in touch and speak with one of our team today.